Cyber Weapons
So called cyber weapons are named as such because they are used to fight “enemies.” These weapons can spy on people or cause major damage by either causing direct damage such as overloading a power plant or opening the floodgates of a dam, or denial of service, such as causing an airliner’s controls to shut down or a central bank to make huge bogus transactions.
All of these weapons are software based, and though some are highly sophisticated, they are not magical or so esoteric to the point it takes an army of PhDs and industrial level manufacturing to develop them like the Manhattan project.
What it does take is competence and persistence, two thing highly available to any government, company, group or community on earth.
By competence I mean you need people with a relatively high level of computer systems understanding. These skills are not in abundance but there is plenty talent around. When I say persistence, I mean those willing to do the tedious work of reverse engineering and looking for vulnerabilities, and vigorously testing and refining software. Any company making a software product needs exactly these same skills and they aren’t all geniuses.
The hard part is already done. Vulnerabilities have been unintentionally built into software since day one, and astonishingly, because of lack of concern for security, vulnerabilities continue to be built in to this day.
Nation-state cyber warfare and spying agencies have a couple of things going for them that no one else does. They can legally gain access to systems through the courts and semi-legally through the cooperation of private companies. This is the great power of the NSA, FBI, DHS, and other three letter organizations in the government of the US. Foreign governments do this as well, it’s not just the US.
And lastly, private companies do this too, and you agreed to be spied on when you decided to use their software. Smartphones and tablet computers were designed to collect information from you. Google, Facebook and Apple have more information about you than any government. Should we worry about that?
Posted in Cyber Security by Mark with comments disabled.
“Digital Arms Dealers” in Spotlight
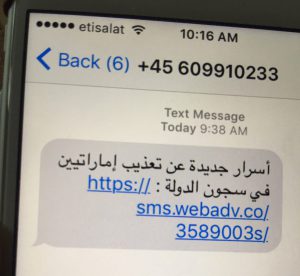
According to the Citizen Lab Website this message reads: “New secrets about torture of Emiratis in state prisons”). The sender’s phone numbers are spoofed.
Last week Apple did an unplanned update of iPads and iPhones to 9.3.5 to fix three security vulnerabilities. While this is hardly news in itself, the way these software flaws were revealed raises a lot of questions.
The security vulnerabilities, due to flaws in the IOS software, were discovered by Citizen Lab at the request of the United Arab Emirates (UAE) human rights activist Ahmed Mansoor. What happened is that Mansoor received an intriguing text message with a link (above photo). Mansoor did not recognize the number and though it contained a tempting message, he did not follow the link but instead requested that Citizen Lab analyze it.
What Citizen Lab found was alarming. They clicked on the link to see what would happen on their phones in the lab. What they found was the link took advantage of the three so called zero day vulnerabilities in IOS to infect it with “advanced” malware used to turn the phone into a spying device. The malware took over the camera and microphone. It could retrieve email, contacts, location, messages and really anything on the phone and send it to a remote server. When this malware is loaded, the phone is “owned” by the writers of the malware. Lesson: NEVER click on a link in an email or text message, whether you think you know the sender or not!
There is really only one attribution for this hack, the UAE government. They were the only ones to be even remotely threatened by Mansoor. So what of it? Don’t repressive governments around the world spy on their citizens all the time?
Well, the malware was apparently a tool sold by a private company called the NSO Group. This is an Israeli founded company but apparently owned by an American company, Francisco Partners.
I have personally had many dealings with the Israeli cybersecurity community since 2006 and can assure you that they have the talent and incentive to form such a company, and there are several other private companies doing this as well. They appear to be selling their hacking tools to foreign governments, who then use the malware to spy. What this means is that a small country does not need a large spying agency such as the NSA, it just needs money.
Obtaining and using unauthorized access of computing systems is a crime in the United States and elsewhere. As a private American citizen, you cannot legally hack into anyone’s computer anywhere in the world. But, apparently as an American you can own and profit from a company that does just that.
Posted in Cyber Security by Mark with comments disabled.
The National Security Agency’s Cyberweapon Leak
What Is Going On with the NSA?
The recent news stories about the cyber weapon leak by a group known as The Shadow Brokers is quite disturbing if true. The story is that this group “hacked” the National Security Agency, appropriated some advanced cyber weapons, and are now auctioning them to the highest bidder online.
The overriding questions are:
Is this real?
How did they do it?
Who are (or is) The Shadow Brokers?
Due to all the secrecy surrounding such agencies, we will probably never know for certain what has happened here, if anything. However, there is a large enough, highly skilled and credible cyber security community today that does not work for the government and their collective opinion should be highly regarded.
The consensus opinion is that yes, these are real weapons, though vintage 2013 or earlier and not the latest. They mention weapon names referred to in the leaked NSA ANT catalog. There is a lot of evidence that this catalog is real and was not leaked by Snowden, but some other NSA insider. I have an earlier post about how security measures I implemented in a product prevented the NSA from gaining access and thus “defeated” the IRATEMONK product in the ANT catalog.
The authenticity of the weapons was supported by evidence from The Guardian, who has access to all of Edward Snowden’s leaked NSA data. The Guardian has not publicly released all the Snowden files and it was confirmed that some information not released to the public was mentioned in the Shadow Broker’s data. There were other more subtle clues as well that pointed to these as being real NSA hacking tools.
How was the NSA hacked? No one knows for sure but most think the actual NSA wasn’t hacked, per se, but the tools were found, or taken from, a proxy server. This could have happened if the NSA was doing training “in the wild” and got sloppy and left their tools on a server instead of cleaning them up. Someone then found them. This is Snowden’s theory.
So who are (or is) The Shadow Brokers? A good theory is that the NSA has yet another insider taking information a la Snowden. It probably had nothing to do with Snowden, by the way, since the tools are dated about 6 months post-Snowden revelations. Another good theory is that a nation-state is taunting the US. Could be Russia. Could be China. Really, it could be Pakistan for all anyone knows about that. It’s very difficult to attribute such attacks in cyber space.
It really doesn’t matter who the hackers are if the NSA is getting this sloppy. How many spy agency leaks have you heard about from Russia? From Israel? From China or North Korea? Probably none. They all have spy agencies on par with the NSA, as do many countries.
Consider the danger of cyber weapons. They are probably as dangerous as physical weapons like missiles and nuclear bombs, especially to advanced, internet driven societies such as the USA, Europe and Japan. Yet cyber weapons are very much unlike physical weapons in that you cannot contain or control them. The NSA relies on secrecy and whether their employees follow good security practices and are loyal, and you see where that got them.
And us.
Posted in Cyber Security, Hacking! by Mark with 1 comment.
What is Up With Cyber Security?

“Hacker”
I’m a cyber security expert and find it a fascinating field.
Why?
I decided to make a partial list:
- Cyber security is an emergent property of computers and the internet. No one saw it coming. When I started in this field about ten years ago, it was nearly impossible to get the grand “deciders” to invest even the tiniest amount of security engineering into a product. Regrets abound today.
- The laws around cyber security make it easy to get around them. The internet is global, laws are regional. Hacking that is legal in one country is illegal in another. Hackers located in Ecuador can legally break into US systems.
- Cyber weapons are rapidly becoming the most important weapon in a nation-state’s arsenal, and it takes relatively little investment to develop them. It cost the US $26 billion to develop the first atomic bombs, how many hackers can you hire for that amount of money in China? The nearly complete reliance of the US economy and infrastructure on the internet makes our country the most vulnerable.
- Both hacking (attacking) and security (defending) are simple. Though you have to be technically adept, it does not take a genius to do either. The thing that makes hacking difficult is the tedious search for vulnerabilities, and the thing that makes security difficult is defending the many avenues of attacks that come from the complexity and interconnectivity of devices today. That aside, almost all cyber attacks rely on very simple methods and approaches used on systems with almost no built-in security measures.
- Lastly, it is interesting because you never know what will happen next!
Posted in Cyber Security by Mark with comments disabled.
How I Defeated the NSA!
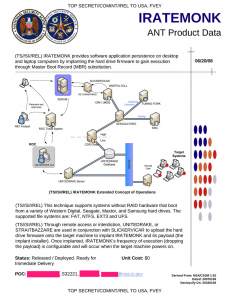
IRATEMONK page from the NSA ANT catalog
Well, maybe “defeat” is too strong of a word, because as Gollum says of the Nazgul, “you cannot defeat them!” BUT, I have ample evidence that measures I put into place years ago made one of my companies products highly resistant to an attack by the NSA. I’ll explain below.
As many of you know, I work as a cyber security researcher and architect. I currently work at a large computer hardware company that I won’t name here, but it’s pretty easy to figure out which one. Back in 2009, I was working on solid state drive (SSD) data security. SSDs are used for local storage, performing the same function as a hard disk drive but using memory chips rather than a magnetic disk to store the data.
Back then, computer security was seen more as a necessary evil rather than an essential primary function of a computer. In other words, the general thought was that you only implement security features if absolutely necessary, it cost money and didn’t generate a visible return on investment. That meant I had the difficult job of trying to convince the “higher ups” that we really need to add security to our products.
I lobbied extensively for a particular security feature called “firmware signing.” This is a technique that uses cryptography to make it difficult to make unauthorized changes to the device firmware. Given that the firmware controls every aspect of a device, this seemed to be essential. Back in 2009, most if not all hard disk drives and SSDs did not use signing. This is a very bad thing!
Consider that if just anyone could update your firmware, they could simply wipe it out or erase all your data. Or they could plant some malicious code to spy on you. This could happen surreptitiously over the internet while you visit a website, for example.
Anyway, I was able to convince, cajole and outright usurp my management at the time to put this security in place. I was successful, but viewed more as a pain-in-the-ass rather than a “savior,” simply because there was no short-term payback.
Fast forward to today. Malware and spyware is everywhere, it is a multi-billion dollar industry worldwide and involves everyone from mischievous teens to highly organized criminal enterprises to nation-states. The security posture of our computer network is pathetic, but getting better.
In May, I saw a report that mentioned The Equation Group and how they exploit firmware. The name “Equation Group” is made up by security researchers who found and classified the malware. To quote the report,
“The ‘Equation Group,’ named for its affinity for ultrasophisticated encryption schemes and associated malware, is now among the most sophisticated threats ever observed.”
Thus, because of it’s sophistication, it is associated with a nation-state attacker, meaning the government of a country. Other evidence, such as the page from the leaked NSA ANT catalog, an internal NSA catalog of spy instruments and software, indicates that this is probably the work of the National Security Agency. The particular product that attacks hard drive or SSD firmware is the IRATEMONK, shown at the top of this post.
So… What evidence do I have that I defeated the NSA? The list of drives known to have been infected by The Equation Group (probably NSA) come from companies such as Seagate, Maxtor, Western Digital, Samsung, IBM, Micron and Toshiba. My company is NOT on that list, and it is likely because of the firmware signing I pushed through way back 2009 when almost no one thought this possible.
Given the secretive nature of this business, that is probably as good of evidence you can get to prove you did your job well!
Posted in Cyber Security by Mark with comments disabled.